Surveillance through smartphones.
Ben Lovejoy from 9to5Mac:
The Indian government has ordered Apple and other smartphone manufacturers to pre-install a state-owned “security” app on all phones before they are sold to users.
Adding fuel to the privacy fire, the government is also requiring smartphone makers to ensure that the app cannot be removed by users …
Reuters reports that those who already own iPhones won’t escape either: Apple and others are also being instructed by the Department of Telecommunications (DoT) to push the app to existing phones via a software update. […]
Apple is likely to push back, hoping to persuade the government to agree to a less extreme policy like offering the app to users during setup and allowing wording that encourages them to install it.
However, ultimately, if negotiations are unsuccessful, it will have to comply with the law. Apple has already been forced to compromise user privacy in China by storing iCloud data on servers owned by a company directly linked to the Chinese government. Apple has also removed VPN and foreign news apps from its Chinese App Store when instructed to do so.
As with China, Apple is in a double-bind here as India is not only a growing market for the company’s products, but also an increasingly important manufacturing centre. Withdrawing from that market in order to uphold its values is not a practical option.
Saw this news story the same day I watched the Mrwhosetheboss’s North Korea video, showing the extreme control North Korea has over their citizens.
Something tells me that even though most world leaders condemn North Korea, they secretly would like to have just as much control over the people.
Ben Lovejoy from 9to5Mac:
The Indian government has ordered Apple and other smartphone manufacturers to pre-install a state-owned “security” app on all phones before they are sold to users.
Adding fuel to the privacy fire, the government is also requiring smartphone makers to ensure that the app cannot be removed by users …
Reuters reports that those who already own iPhones won’t escape either: Apple and others are also being instructed by the Department of Telecommunications (DoT) to push the app to existing phones via a software update. […]
Apple is likely to push back, hoping to persuade the government to agree to a less extreme policy like offering the app to users during setup and allowing wording that encourages them to install it.
However, ultimately, if negotiations are unsuccessful, it will have to comply with the law. Apple has already been forced to compromise user privacy in China by storing iCloud data on servers owned by a company directly linked to the Chinese government. Apple has also removed VPN and foreign news apps from its Chinese App Store when instructed to do so.
As with China, Apple is in a double-bind here as India is not only a growing market for the company’s products, but also an increasingly important manufacturing centre. Withdrawing from that market in order to uphold its values is not a practical option.
Saw this news story the same day I watched the Mrwhosetheboss’s North Korea video, showing the extreme control North Korea has over their citizens.
Something tells me that even though most world leaders condemn North Korea, they secretly would like to have just as much control over the people.
EE, a UK based mobile network operator, will have new family plans that limit internet usage for teenagers - as long as they don’t use Wi-Fi.
BBC:
Its new Sim-only mobile plans will filter the web at different levels depending on the age of the child using it, with three separate tiers of protections.
The plans will also have other features such as reduced internet speeds for younger teens to "limit streaming", as well as protecting against scam calls.
But EE can only control what is accessed by using mobile data using its network - meaning it cannot filter content accessed via wi-fi, which is operated separately.
Sounds like a way to profit off of parents’ fears and desire to do what’s right for their kids, but the uptake of many of these parental controls is really slim. Even on iPhone, setting up Screen Time and Parental Controls is cumbersome, and it took several tries for me to get things right for my kids. It also doesn’t help that you have to remember another 4-digit passcode.
I’m not alone in this battle:
EE ambassador and TV presenter Konnie Huq said at a launch event for the new plans she felt "like her mum in the old days" - who she recalled struggling to work the family's TV remote controls.
Meta, which owns Instagram and WhatsApp, says take-up of its numerous parental controls is relatively low.
Technology analyst Paolo Pescatore told the BBC that EE's plans are "a huge step in the right direction" but implementation of such controls "is no easy feat."
The best option really is to use on-device tools or a third party tool that works cross-platform and master that one app. For me, that’s Screen Time and Parental Controls on Apple devices, for now.
Another real risk of these plans - funneling kids to use public Wi-Fi more than usual, which is a whole different set of risks.
BBC:
Its new Sim-only mobile plans will filter the web at different levels depending on the age of the child using it, with three separate tiers of protections.
The plans will also have other features such as reduced internet speeds for younger teens to "limit streaming", as well as protecting against scam calls.
But EE can only control what is accessed by using mobile data using its network - meaning it cannot filter content accessed via wi-fi, which is operated separately.
Sounds like a way to profit off of parents’ fears and desire to do what’s right for their kids, but the uptake of many of these parental controls is really slim. Even on iPhone, setting up Screen Time and Parental Controls is cumbersome, and it took several tries for me to get things right for my kids. It also doesn’t help that you have to remember another 4-digit passcode.
I’m not alone in this battle:
EE ambassador and TV presenter Konnie Huq said at a launch event for the new plans she felt "like her mum in the old days" - who she recalled struggling to work the family's TV remote controls.
Meta, which owns Instagram and WhatsApp, says take-up of its numerous parental controls is relatively low.
Technology analyst Paolo Pescatore told the BBC that EE's plans are "a huge step in the right direction" but implementation of such controls "is no easy feat."
The best option really is to use on-device tools or a third party tool that works cross-platform and master that one app. For me, that’s Screen Time and Parental Controls on Apple devices, for now.
Another real risk of these plans - funneling kids to use public Wi-Fi more than usual, which is a whole different set of risks.
Taiwan’s TSMC chip technology leak is a bigger deal than you think.
Bloomberg (paywalled article):
Taiwan prosecutors arrested six people suspected of stealing trade secrets from Taiwan Semiconductor Manufacturing Co., opening an investigation into a potential breach of national security involving a global tech industry linchpin.
The chipmaker to Nvidia Corp. reported a number of former and current staff to authorities on suspicion they illegally obtained core technology. A total of six people were arrested, with two posting bail and one released afterwards, said Taiwan High Prosecutors Office spokesman John Nieh. Prosecutors searched the homes of some staff between July 25 and July 28, the agency said in a statement. It’s now trying to find out if data had been leaked to other parties.
TSMC is the world’s most advanced maker of semiconductors, from Nvidia AI accelerators to Apple Inc. iPhone processors. The case coincides with a quickening race by the likes of Meta Platforms Inc.and DeepSeek to develop artificial intelligence in the post-ChatGPT era, which requires billions of dollars in servers and datacenters.
On Tuesday, the Nikkei reported that TSMC fired several employees suspected of trying to obtain critical information on 2-nanometer chip development. That next-generation semiconductor process is entering mass production in the second half of this year.
TSMC is more than just a chip maker. They’re literally responsible for running the global economy. China believes Taiwan is part of China, and are very eager to seek “reunification” with the island, calling it sacred territory.
An excerpt from Apple in China by Patrick McGee:
When on October 1, 2024, the Communist Party celebrated seventy-five years of ruling China, Xi reiterated his desire to "reunify" with the island democracy, saying "Taiwan is China's sacred territory" and that the two are connected by blood. "It's an irreversible trend, a cause of righteousness and the common aspiration of the people," he told thousands of supporters. "No one can stop the march of history.”
Any military action would immediately threaten TSMC, which is responsible for making at least 80 percent of the world's most advanced chips. In war games involving an invasion of Taiwan by China, Taiwan's semiconductor industry doesn't survive. "It would go out of business on day one of the war," according to Chris Miller, author of Chip War. "The moment fighting starts, TSMC facilities would stop producing. It would never be reopened." Such a cessation in production would have disastrous effects on the world economy. Avril Haines, US director of national intel-ligence, estimates that if Taiwan were prevented from exporting chips, the global loss would be "somewhere between $600 billion to more than $1 trillion, on an annual basis, for the first several years." Indeed, the New York Times columnist Nicholas Kristof has credibly called TSMC "the only corporation... in history that could cause a global depression if it were forced to halt production." For Apple alone, the impact would be the equivalent of a meteor strike.
According to the article, China is still manufacturing 7-nanometer chips while TSMC is working on more efficient 2-nanometer chips.
The headline sounds like another routine stolen trade secrets scandal, but it’s more cutthroat than that (pun intended).
They don’t call it the Chip Wars for nothing.
Bloomberg (paywalled article):
Taiwan prosecutors arrested six people suspected of stealing trade secrets from Taiwan Semiconductor Manufacturing Co., opening an investigation into a potential breach of national security involving a global tech industry linchpin.
The chipmaker to Nvidia Corp. reported a number of former and current staff to authorities on suspicion they illegally obtained core technology. A total of six people were arrested, with two posting bail and one released afterwards, said Taiwan High Prosecutors Office spokesman John Nieh. Prosecutors searched the homes of some staff between July 25 and July 28, the agency said in a statement. It’s now trying to find out if data had been leaked to other parties.
TSMC is the world’s most advanced maker of semiconductors, from Nvidia AI accelerators to Apple Inc. iPhone processors. The case coincides with a quickening race by the likes of Meta Platforms Inc.and DeepSeek to develop artificial intelligence in the post-ChatGPT era, which requires billions of dollars in servers and datacenters.
On Tuesday, the Nikkei reported that TSMC fired several employees suspected of trying to obtain critical information on 2-nanometer chip development. That next-generation semiconductor process is entering mass production in the second half of this year.
TSMC is more than just a chip maker. They’re literally responsible for running the global economy. China believes Taiwan is part of China, and are very eager to seek “reunification” with the island, calling it sacred territory.
An excerpt from Apple in China by Patrick McGee:
When on October 1, 2024, the Communist Party celebrated seventy-five years of ruling China, Xi reiterated his desire to "reunify" with the island democracy, saying "Taiwan is China's sacred territory" and that the two are connected by blood. "It's an irreversible trend, a cause of righteousness and the common aspiration of the people," he told thousands of supporters. "No one can stop the march of history.”
Any military action would immediately threaten TSMC, which is responsible for making at least 80 percent of the world's most advanced chips. In war games involving an invasion of Taiwan by China, Taiwan's semiconductor industry doesn't survive. "It would go out of business on day one of the war," according to Chris Miller, author of Chip War. "The moment fighting starts, TSMC facilities would stop producing. It would never be reopened." Such a cessation in production would have disastrous effects on the world economy. Avril Haines, US director of national intel-ligence, estimates that if Taiwan were prevented from exporting chips, the global loss would be "somewhere between $600 billion to more than $1 trillion, on an annual basis, for the first several years." Indeed, the New York Times columnist Nicholas Kristof has credibly called TSMC "the only corporation... in history that could cause a global depression if it were forced to halt production." For Apple alone, the impact would be the equivalent of a meteor strike.
According to the article, China is still manufacturing 7-nanometer chips while TSMC is working on more efficient 2-nanometer chips.
The headline sounds like another routine stolen trade secrets scandal, but it’s more cutthroat than that (pun intended).
They don’t call it the Chip Wars for nothing.
The best passcode for a lazy person is a 5-digit passcode.
If you use the standard 4-digit or 6-digit passcode formats on the iPhone, you get the equivalent amount of bubbles on your lock screen, showing anyone who even glances at your phone how long your passcode is before you even start pressing buttons.
If you select a “Custom Numeric Code” when adding or changing your passcode, you can just type a 5-digit code and your lock screen will now show an empty box that doesn’t give away the length of your passcode. Sure you would have to hit the “OK” button afterwards, but it’s still the safer option.
You can’t go less than 4 digits. I tried.
If you use the standard 4-digit or 6-digit passcode formats on the iPhone, you get the equivalent amount of bubbles on your lock screen, showing anyone who even glances at your phone how long your passcode is before you even start pressing buttons.
If you select a “Custom Numeric Code” when adding or changing your passcode, you can just type a 5-digit code and your lock screen will now show an empty box that doesn’t give away the length of your passcode. Sure you would have to hit the “OK” button afterwards, but it’s still the safer option.
You can’t go less than 4 digits. I tried.
Quickly disabling biometrics on Android is literally several steps behind iOS.
Imagine if your car required you to slam on the brakes as hard as you can and tap an “anti-lock brakes” button on your infotainment screen in order to activate the anti-lock brakes.
That’s essentially what Android phones require you to do in order to quickly disable biometrics. It is not an intuitive, one-step process on Android like it is on the iPhone.
First, you have to enable Lockdown Mode in Settings by either searching for “Lockdown Mode,” or going through a menu tree depending which Android phone you have.
That is assuming of course, your Android phone even supports it.
Seems like Samsung requires you to enable Lockdown Mode first through this menu tree, but it’s a one-time operation so I’ll let that pass. Once you have done that, you can hold the power button until you get to the power menu screen, and then tap the Lockdown button.
On Pixel phones, if your power button isn’t tied to Google Assistant, you can press and hold the power button to get into the power menu, and then select Lockdown. If your power button activates Google Assistant like an iPhone’s power button activates Siri, then you have to press and hold volume up and the power button and then you enter the power menu and have to select Lockdown.
You don’t get a one-step method like iOS, where a simple press and hold of the Power Button on one side of the device, and any or both volume buttons on the other side of the device (essentially squeezing the phone) automatically disables all biometrics. Just press and hold for a full 2 seconds, and that’s it.
No touchscreen input required.
If you have Haptics turned on, you also get a vibration to confirm your button inputs were successful. Personally, it’s best to enable Haptics to give you more reassurance.
Haptics or not, the point is you don’t have to look at your iPhone’s screen and confirm anything with a touch, which in my opinion defeats the purpose of quickly securing your device. That I won’t let pass.
You also don’t have to think about which volume button to press on an iPhone, since either one (or both together) will work. Just squeeze the damn iPhone and you’re good.
Odds are if you are in a situation where you have to do this, you’re already distraught to some extent, and might not have the time to even touch your screen if someone grabs the phone out of your hands fast enough.
Once again, assuming you even enabled Lockdown Mode.
Imagine if your car required you to slam on the brakes as hard as you can and tap an “anti-lock brakes” button on your infotainment screen in order to activate the anti-lock brakes.
That’s essentially what Android phones require you to do in order to quickly disable biometrics. It is not an intuitive, one-step process on Android like it is on the iPhone.
First, you have to enable Lockdown Mode in Settings by either searching for “Lockdown Mode,” or going through a menu tree depending which Android phone you have.
That is assuming of course, your Android phone even supports it.
Seems like Samsung requires you to enable Lockdown Mode first through this menu tree, but it’s a one-time operation so I’ll let that pass. Once you have done that, you can hold the power button until you get to the power menu screen, and then tap the Lockdown button.
On Pixel phones, if your power button isn’t tied to Google Assistant, you can press and hold the power button to get into the power menu, and then select Lockdown. If your power button activates Google Assistant like an iPhone’s power button activates Siri, then you have to press and hold volume up and the power button and then you enter the power menu and have to select Lockdown.
You don’t get a one-step method like iOS, where a simple press and hold of the Power Button on one side of the device, and any or both volume buttons on the other side of the device (essentially squeezing the phone) automatically disables all biometrics. Just press and hold for a full 2 seconds, and that’s it.
No touchscreen input required.
If you have Haptics turned on, you also get a vibration to confirm your button inputs were successful. Personally, it’s best to enable Haptics to give you more reassurance.
Haptics or not, the point is you don’t have to look at your iPhone’s screen and confirm anything with a touch, which in my opinion defeats the purpose of quickly securing your device. That I won’t let pass.
You also don’t have to think about which volume button to press on an iPhone, since either one (or both together) will work. Just squeeze the damn iPhone and you’re good.
Odds are if you are in a situation where you have to do this, you’re already distraught to some extent, and might not have the time to even touch your screen if someone grabs the phone out of your hands fast enough.
Once again, assuming you even enabled Lockdown Mode.
Google follows Apple and updates Android devices to auto-reboot after 3 days for security purposes.
On Monday, the tech giant pushed updates to Google Play services, a core part of Android that provides functionalities for apps and the operating system itself. Listed under “Security & Privacy” is a new security feature that “will automatically restart your device if locked for 3 consecutive days.”
Last year, Apple rolled out the same feature for iOS. The thinking behind adding an automatic reboot after a certain period of inactivity is to make life more difficult for someone who is trying to unlock or extract data from a phone; for example, law enforcement using a forensic analysis device like those made by Cellebrite or Magnet Forensics.
Before a phone is switched on and unlocked, certain data stored within is fully encrypted and harder to access without the user’s passcode. This is known as the “Before First Unlock” state. Once unlocked, on the other hand, some data gets decrypted and can potentially be accessed by bruteforcing the passcode or taking advantage of security flaws, which is generally how law enforcement forensic devices work. This state is known as “After First Unlock.”
The early sluggishness of Android system updates prompted Google to begin moving parts of the OS to Google Play Services. This collection of background services and libraries can be updated by Google automatically in the background as long as your phone is certified for Google services (which almost all are). That's why the inactivity reboot will just show up on your phone in the coming weeks with no notification.
Great update that will come to all Android devices since it’s tied to Google Play Services and not a specific version of Android.
On Monday, the tech giant pushed updates to Google Play services, a core part of Android that provides functionalities for apps and the operating system itself. Listed under “Security & Privacy” is a new security feature that “will automatically restart your device if locked for 3 consecutive days.”
Last year, Apple rolled out the same feature for iOS. The thinking behind adding an automatic reboot after a certain period of inactivity is to make life more difficult for someone who is trying to unlock or extract data from a phone; for example, law enforcement using a forensic analysis device like those made by Cellebrite or Magnet Forensics.
Before a phone is switched on and unlocked, certain data stored within is fully encrypted and harder to access without the user’s passcode. This is known as the “Before First Unlock” state. Once unlocked, on the other hand, some data gets decrypted and can potentially be accessed by bruteforcing the passcode or taking advantage of security flaws, which is generally how law enforcement forensic devices work. This state is known as “After First Unlock.”
The early sluggishness of Android system updates prompted Google to begin moving parts of the OS to Google Play Services. This collection of background services and libraries can be updated by Google automatically in the background as long as your phone is certified for Google services (which almost all are). That's why the inactivity reboot will just show up on your phone in the coming weeks with no notification.
Great update that will come to all Android devices since it’s tied to Google Play Services and not a specific version of Android.
You can still access your Wallet while hard-locking your iPhone.
After discussing hard-locking your iPhone a few days ago, it turns out you can still use the Wallet app by double-clicking the Power Button to access your boarding passes, membership cards, and Driver’s License in participating states.
You can also pay with Apple Pay, but you would have to enter your Passcode which I would argue is more dangerous in that situation since you’re probably around other people.
You learn something new everyday.
After discussing hard-locking your iPhone a few days ago, it turns out you can still use the Wallet app by double-clicking the Power Button to access your boarding passes, membership cards, and Driver’s License in participating states.
You can also pay with Apple Pay, but you would have to enter your Passcode which I would argue is more dangerous in that situation since you’re probably around other people.
You learn something new everyday.
How to Temporarily Disable Face ID or Touch ID, and Require a Passcode to Unlock Your iPhone or iPad (2025 edition).
There’s never a bad time (and always a good time) to be reminded of this feature.
I copied the title straight from Gruber’s website, and it’s best just to read his description since I couldn’t put it any better. His almost 3-year-old article still holds up well, especially in today’s day and age:
The problem is this: if you use Face ID or Touch ID on your device (and you almost certainly should), what happens if law enforcement (or anyone else for that matter) takes your device and physically forces you to unlock it biometrically? There is some legal precedent supporting the notion that police can force you to do this, but can’t force you to provide them with a passcode or passphrase.
Here are two essential things everyone should know.
The first is hard-locking. When you hard-lock your iPhone or iPad, it enters a mode that requires the device passcode to unlock. With recent iPhones and iPads, you enter this mode the same way that you turn off the device: by pressing and holding the power button and either of the volume buttons for about two seconds.* You’ll know when you’ve pressed the buttons long enough because there’s haptic feedback.** This takes you to the screen where you see a slider to power down the device, and on iPhones, where you can initiate an Emergency SOS call or view the device owner’s Medical ID (if they have one). The important thing to note is that you don’t have to do anything on this screen to hard-lock your device — once you’ve gotten to this screen, the device is already hard-locked and will require the passcode to unlock. You can’t use Face ID or Touch ID again until the passcode has been entered. This is important because it means you can easily hard-lock your iPhone without even looking at it, or removing it from your pocket or purse. That you can do this surreptitiously is very much by design.
Just press and hold the buttons on both sides. Remember that. Try it now. Don’t just memorize it, internalize it, so that you’ll be able to do it without much thought while under duress, like if you’re confronted by a police officer. Remember to do this every time you’re separated from your phone, like when going through the magnetometer at any security checkpoint, especially airports. As soon as you see a metal detector ahead of you, you should think, “Hard-lock my iPhone”.
The second thing is to know your rights. Never ever hand your phone to a cop or anyone vaguely cop-like, like the rent-a-cops working for TSA. If they tell you that you must, refuse. They can and will lie to you about this. If you really need to hand it over, they’ll take it from you. And they won’t get anything from it, because you’ll have already hard-locked it, and you’ll know that you cannot be required to give them your passcode.
* You can also do the same thing by quickly pressing the side button alone five times. On older iPhones (iPhone 7 and earlier), rapidly pressing the side button five times will immediately initiate the SOS phone call to emergency services; on iPhone 8 and later it just takes you to the same lock screen as when you press and hold the side button along with a volume button. I find the press-and-hold method easier to remember. I think of it as squeezing my iPhone for a moment to protect its contents.
**This haptic feedback/confirmation only occurs if “Vibrate on Ring” is turned on in Settings → Sounds & Haptics. I feel like this haptic feedback should occur regardless of this setting.
The only thing that needs a minor update is his second footnote, which has changed with iOS updates. Under Settings > Sounds & Haptics > Haptics, you now have four different options:
Always Play
Play in Silent Mode
Don’t Play in Silent Mode
Never Play
Keep your Haptics on “Always Play” so you can always feel the confirmation for hard-locking your device even though it is out of sight, regardless of Silent Mode.
The last thing you want is to second guess yourself and think, “is my iPhone actually hard-locked or not?”
For the iPad, there is no Haptics option, so holding the power button and either volume button (or both volume buttons) for 2 seconds is enough.
There’s never a bad time (and always a good time) to be reminded of this feature.
I copied the title straight from Gruber’s website, and it’s best just to read his description since I couldn’t put it any better. His almost 3-year-old article still holds up well, especially in today’s day and age:
The problem is this: if you use Face ID or Touch ID on your device (and you almost certainly should), what happens if law enforcement (or anyone else for that matter) takes your device and physically forces you to unlock it biometrically? There is some legal precedent supporting the notion that police can force you to do this, but can’t force you to provide them with a passcode or passphrase.
Here are two essential things everyone should know.
The first is hard-locking. When you hard-lock your iPhone or iPad, it enters a mode that requires the device passcode to unlock. With recent iPhones and iPads, you enter this mode the same way that you turn off the device: by pressing and holding the power button and either of the volume buttons for about two seconds.* You’ll know when you’ve pressed the buttons long enough because there’s haptic feedback.** This takes you to the screen where you see a slider to power down the device, and on iPhones, where you can initiate an Emergency SOS call or view the device owner’s Medical ID (if they have one). The important thing to note is that you don’t have to do anything on this screen to hard-lock your device — once you’ve gotten to this screen, the device is already hard-locked and will require the passcode to unlock. You can’t use Face ID or Touch ID again until the passcode has been entered. This is important because it means you can easily hard-lock your iPhone without even looking at it, or removing it from your pocket or purse. That you can do this surreptitiously is very much by design.
Just press and hold the buttons on both sides. Remember that. Try it now. Don’t just memorize it, internalize it, so that you’ll be able to do it without much thought while under duress, like if you’re confronted by a police officer. Remember to do this every time you’re separated from your phone, like when going through the magnetometer at any security checkpoint, especially airports. As soon as you see a metal detector ahead of you, you should think, “Hard-lock my iPhone”.
The second thing is to know your rights. Never ever hand your phone to a cop or anyone vaguely cop-like, like the rent-a-cops working for TSA. If they tell you that you must, refuse. They can and will lie to you about this. If you really need to hand it over, they’ll take it from you. And they won’t get anything from it, because you’ll have already hard-locked it, and you’ll know that you cannot be required to give them your passcode.
* You can also do the same thing by quickly pressing the side button alone five times. On older iPhones (iPhone 7 and earlier), rapidly pressing the side button five times will immediately initiate the SOS phone call to emergency services; on iPhone 8 and later it just takes you to the same lock screen as when you press and hold the side button along with a volume button. I find the press-and-hold method easier to remember. I think of it as squeezing my iPhone for a moment to protect its contents.
**This haptic feedback/confirmation only occurs if “Vibrate on Ring” is turned on in Settings → Sounds & Haptics. I feel like this haptic feedback should occur regardless of this setting.
The only thing that needs a minor update is his second footnote, which has changed with iOS updates. Under Settings > Sounds & Haptics > Haptics, you now have four different options:
Always Play
Play in Silent Mode
Don’t Play in Silent Mode
Never Play
Keep your Haptics on “Always Play” so you can always feel the confirmation for hard-locking your device even though it is out of sight, regardless of Silent Mode.
The last thing you want is to second guess yourself and think, “is my iPhone actually hard-locked or not?”
For the iPad, there is no Haptics option, so holding the power button and either volume button (or both volume buttons) for 2 seconds is enough.
How to quickly and easily tell if an iPhone is genuine before opening the box.
There’s an easy way to check an iPhone 15 or later box to see if what you’re buying is genuine or a fake. All you need is a cheap UV light pen to see the hidden markers. 📓
There’s an easy way to check an iPhone 15 or later box to see if what you’re buying is genuine or a fake. All you need is a cheap UV light pen to see the hidden markers.
Starting with the iPhone 15, Apple made these hidden markers to help thwart off fake iPhones that are all over the markets. There is a QR code, and an “ iPhone” symbol that is only visible with UV light. With the iPhone 15, the QR code and “ iPhone” markers are one on top of another, so when you peel off the tabs, the “ iPhone” gets discarded leaving only the QR code. Take a look at a new iPhone 15 Plus box vs. an opened 15 Pro Max box for comparison:
On the iPhone 16, both the QR code and “ iPhone” markers are on the same line, so nothing gets discarded after opening the package. Here is a new 16 Plus vs. an opened 16 Pro Max:
There is another QR code at the bottom of the box that you can check in case there are some stickers covering the top areas. It is in the same place on all iPhones.
This applies to all iPhone 15 or later models, and I’m assuming the iPhone 16e too. These are for iPhones worldwide and not just the USA because I have the following iPhones from the following countries that all have these markings:
15 Pro Max purchased in Saudi Arabia.
16 Pro Max purchased in Toronto.
15 Plus and 16 Plus purchased in USA. (Wife has to decide which one she likes based on color 🧐).
I posted this information on X a few days ago, and it seems that even the scammers have caught up and put these same hidden markings on their boxes. From what I have seen online though, that is not the case and most fake iPhones don’t have these markings because, who really carries a UV light pen with them?
By the way a UV light pen is only a few bucks on Amazon, or you can just ask your daughter or niece if you could borrow her invisible ink spy pen because odds are they have one (my daughter did!).
That being said, this is the quickest and easiest way to determine if an iPhone you’re buying is fake. Nothing is guaranteed until you open the box and boot up the device, but one thing to know for sure is, if you don’t see these markings on an iPhone 15 or 16 box, it is a fake.
GM’s Apple CarPlay issues get worse.
There was one GM dealership in the whole United States that was allowed to install a “phone-mirroring system” to allow Android Auto and Apple CarPlay back inside GM’s EVs, but now that has been defunct.
Nico Demattia from TheDrive:
For some frustrated owners of GM‘s new electric cars, White Automotive seemed like a lifesaver. After GM decided to drop Apple CarPlay and Android Auto support in its Ultium-platform EVs, and soon its entire lineup, White stepped up with an aftermarket setup that dealers could install to restore both phone-mirroring systems to those models for new buyers. But that effort has already met its predictable end, as GM recently pushed the only Chevy dealer in the country that was installing them to stop—thereby also forcing White Automotive to discontinue the kit.
A source within GM confirmed to The Drive that the automaker had investigated how the integration was being done and found that it could have adverse impacts on “critical” vehicle functions and stop working altogether with future software updates. Meanwhile, the dealer in question—LaFontaine Chevrolet in Plymouth, Michigan—told us that GM instructed them to stop offering and installing White’s kit. And without that distribution channel, or any chance of getting another dealer on board, White Automotive—who declined to comment directly for this story—had to shut down the project.
Considering this aftermarket system gave users full control of the entire dash including the gauge cluster, it is a high-risk and safety concern if something were to go wrong.
The kit supported both wired and wireless projection for Apple and Google’s smartphones and integrated them across the cars’ infotainment screens, digital gauge clusters, and heads-up displays. It was a comprehensive implementation; drivers could even summon Siri or Google Assistant just as they would if those features were integrated from the factory.
Quite frankly, I’m surprised GM even allowed this one dealership to perform these installations. If they have a hard stance against CarPlay and Android Auto, just stick to it and don’t give people false hope that there is a solution. Now these poor customers are out probably several grand with hardware that is obsolete overnight:
If you check the listing on the company’s page now, its title merely reads, “This product has been discontinued,” and the associated image is blank. Below, a statement addressed to “valued customers,” reads:
“We have made the difficult decision to discontinue this product. Rather than removing it from our website entirely, we wanted to leave this notice so customers are aware of its discontinuation. This was not a decision we made lightly, but due to a variety of factors, continuing to offer this product is no longer viable in the long term.”
Where is the EU when you need them?
There was one GM dealership in the whole United States that was allowed to install a “phone-mirroring system” to allow Android Auto and Apple CarPlay back inside GM’s EVs, but now that has been defunct.
Nico Demattia from TheDrive:
For some frustrated owners of GM‘s new electric cars, White Automotive seemed like a lifesaver. After GM decided to drop Apple CarPlay and Android Auto support in its Ultium-platform EVs, and soon its entire lineup, White stepped up with an aftermarket setup that dealers could install to restore both phone-mirroring systems to those models for new buyers. But that effort has already met its predictable end, as GM recently pushed the only Chevy dealer in the country that was installing them to stop—thereby also forcing White Automotive to discontinue the kit.
A source within GM confirmed to The Drive that the automaker had investigated how the integration was being done and found that it could have adverse impacts on “critical” vehicle functions and stop working altogether with future software updates. Meanwhile, the dealer in question—LaFontaine Chevrolet in Plymouth, Michigan—told us that GM instructed them to stop offering and installing White’s kit. And without that distribution channel, or any chance of getting another dealer on board, White Automotive—who declined to comment directly for this story—had to shut down the project.
Considering this aftermarket system gave users full control of the entire dash including the gauge cluster, it is a high-risk and safety concern if something were to go wrong.
The kit supported both wired and wireless projection for Apple and Google’s smartphones and integrated them across the cars’ infotainment screens, digital gauge clusters, and heads-up displays. It was a comprehensive implementation; drivers could even summon Siri or Google Assistant just as they would if those features were integrated from the factory.
Quite frankly, I’m surprised GM even allowed this one dealership to perform these installations. If they have a hard stance against CarPlay and Android Auto, just stick to it and don’t give people false hope that there is a solution. Now these poor customers are out probably several grand with hardware that is obsolete overnight:
If you check the listing on the company’s page now, its title merely reads, “This product has been discontinued,” and the associated image is blank. Below, a statement addressed to “valued customers,” reads:
“We have made the difficult decision to discontinue this product. Rather than removing it from our website entirely, we wanted to leave this notice so customers are aware of its discontinuation. This was not a decision we made lightly, but due to a variety of factors, continuing to offer this product is no longer viable in the long term.”
Where is the EU when you need them?
Let me remind you again to record your unboxing videos.
Juli Clover from MacRumors:
The U.S. Department of Justice recently cracked down on an international crime ring that targeted expensive electronics like the iPhone, with the workings of the complex crime system detailed in a report from The Wall Street Journal.
Thirteen members of an international network worked to steal FedEx shipments of iPhones from people's porches, using automated scripts to scrape data from FedEx tracking systems and also bribing corrupt employees from AT&T. The employees took payments to share confidential customer information from a company order tracking system, snapping images of customer names, addresses, and tracking numbers.
Some members of the criminal network obtained and sold delivery information, while others, called runners, purchased that info and physically stole the iPhone packages from doorsteps just minutes after they were delivered.
I didn’t have a porch pirate steal my Apple Watch Ultra 2 that I had shipped from Best Buy, but it was already stolen when it was returned to Best Buy. I bought one in “Open Box Excellent” condition and when I unboxed it, there was no watch inside, even though it still had the pull tabs on it as if it was sealed. You can read about my full experience, but just know that even if your package does manage to make it to your hands, do yourself a huge favor and record your unboxing experiences so you can prove your innocence. Thankfully the Apple Watch band comes in a separate box from the watch, and I was able to record the band unboxing which proved I wasn’t the culprit.
In another instance just a few days later, I ordered a brand new iPhone SE from Apple directly and it came through FedEx. The packaging was suspect. If you order directly from Apple, you know that the shipping box is catered towards the product you’re receiving, and even the shipping box has pull tabs on it similar to the product packaging itself. You never need a knife or have to muscle your way into the box.
Never.
This package had regular clear tape on it, and the piece of tape with the pull tab was tucked underneath the flap, making it useless and showed either signs of tampering, or someone who didn’t apply the tape correctly and decided to put regular tape on it.
I wasn’t taking any chances and decided to record the unboxing experience. This time I wasn’t missing anything, but the question still remains: was someone trying to steal the iPhone and decided it was too risky and just sealed it back up with regular tape, or did someone just improperly put on the pull-tab tape and decide to fix it with some tape? Either way, take a look at what I’m talking about but please record your unboxings.
Juli Clover from MacRumors:
The U.S. Department of Justice recently cracked down on an international crime ring that targeted expensive electronics like the iPhone, with the workings of the complex crime system detailed in a report from The Wall Street Journal.
Thirteen members of an international network worked to steal FedEx shipments of iPhones from people's porches, using automated scripts to scrape data from FedEx tracking systems and also bribing corrupt employees from AT&T. The employees took payments to share confidential customer information from a company order tracking system, snapping images of customer names, addresses, and tracking numbers.
Some members of the criminal network obtained and sold delivery information, while others, called runners, purchased that info and physically stole the iPhone packages from doorsteps just minutes after they were delivered.
I didn’t have a porch pirate steal my Apple Watch Ultra 2 that I had shipped from Best Buy, but it was already stolen when it was returned to Best Buy. I bought one in “Open Box Excellent” condition and when I unboxed it, there was no watch inside, even though it still had the pull tabs on it as if it was sealed. You can read about my full experience, but just know that even if your package does manage to make it to your hands, do yourself a huge favor and record your unboxing experiences so you can prove your innocence. Thankfully the Apple Watch band comes in a separate box from the watch, and I was able to record the band unboxing which proved I wasn’t the culprit.
In another instance just a few days later, I ordered a brand new iPhone SE from Apple directly and it came through FedEx. The packaging was suspect. If you order directly from Apple, you know that the shipping box is catered towards the product you’re receiving, and even the shipping box has pull tabs on it similar to the product packaging itself. You never need a knife or have to muscle your way into the box.
Never.
This package had regular clear tape on it, and the piece of tape with the pull tab was tucked underneath the flap, making it useless and showed either signs of tampering, or someone who didn’t apply the tape correctly and decided to put regular tape on it.
I wasn’t taking any chances and decided to record the unboxing experience. This time I wasn’t missing anything, but the question still remains: was someone trying to steal the iPhone and decided it was too risky and just sealed it back up with regular tape, or did someone just improperly put on the pull-tab tape and decide to fix it with some tape? Either way, take a look at what I’m talking about but please record your unboxings.
You could get phished with Apple’s Passwords app, unless you update to iOS 18.2.
Arin Waichulis from 9to5Mac:
Security researchers at Mysk first discovered the flaw after noticing that their iPhone’s App Privacy Report showed Passwords had contacted a staggering 130 different websites over insecure HTTP traffic. This prompted the duo to investigate further, finding that not only was the app fetching account logos and icons over HTTP—it also defaulted to opening password reset pages using the unencrypted protocol. “This left the user vulnerable: an attacker with privileged network access could intercept the HTTP request and redirect the user to a phishing website,” Mysk told 9to5Mac.
“We were surprised that Apple didn’t enforce HTTPS by default for such a sensitive app,” Mysk states.
Most modern websites nowadays allow unencrypted HTTP connections but automatically redirect them to HTTPS using a 301 redirect. It’s important to note that while the Passwords app before iOS 18.2 would make a request over HTTP, it would redirected to the secure HTTPS version. Under normal circumstances, this would be totally fine, as the password changes occur on an encrypted page, ensuring that credentials are not sent in plaintext.
However, it becomes a problem when the attacker is connected to the same network as the user (i.e. Starbucks, airport, or hotel Wi-Fi) and intercepts the initial HTTP request before it redirects. From here they could manipulate the traffic in a few ways.
Mysk’s video is short but direct and to the point to help visualize how phishing works.
Perfect time for Apple to report this security bug, when all news outlets are focused on Apple Intelligence and Siri’s failures. Also a perfect time to remind your loved ones not to trust public Wi-Fi networks.
Arin Waichulis from 9to5Mac:
Security researchers at Mysk first discovered the flaw after noticing that their iPhone’s App Privacy Report showed Passwords had contacted a staggering 130 different websites over insecure HTTP traffic. This prompted the duo to investigate further, finding that not only was the app fetching account logos and icons over HTTP—it also defaulted to opening password reset pages using the unencrypted protocol. “This left the user vulnerable: an attacker with privileged network access could intercept the HTTP request and redirect the user to a phishing website,” Mysk told 9to5Mac.
“We were surprised that Apple didn’t enforce HTTPS by default for such a sensitive app,” Mysk states.
Most modern websites nowadays allow unencrypted HTTP connections but automatically redirect them to HTTPS using a 301 redirect. It’s important to note that while the Passwords app before iOS 18.2 would make a request over HTTP, it would redirected to the secure HTTPS version. Under normal circumstances, this would be totally fine, as the password changes occur on an encrypted page, ensuring that credentials are not sent in plaintext.
However, it becomes a problem when the attacker is connected to the same network as the user (i.e. Starbucks, airport, or hotel Wi-Fi) and intercepts the initial HTTP request before it redirects. From here they could manipulate the traffic in a few ways.
Mysk’s video is short but direct and to the point to help visualize how phishing works.
Perfect time for Apple to report this security bug, when all news outlets are focused on Apple Intelligence and Siri’s failures. Also a perfect time to remind your loved ones not to trust public Wi-Fi networks.
Apple products: Why you should film your unboxing videos (part 2)
I mentioned earlier how Best Buy was going to give me a refund simply because I told them I didn’t receive a watch inside the package. It turns out I was misinformed by the person who helped me with this case. This actually makes a ton of sense though because if it was as simple as calling Best Buy and telling them there was nothing in the package, what is there to stop anyone from simply abusing that policy? They do want to do an investigation, which makes perfect sense.
They got back to me via email and kindly requested pictures of the product packaging and the shipping box. I one-upped that request with detailed photos and a video of me unboxing the watch strap box, tearing the seals and finding even more overly engineered cardboard.
I do expect to get a full refund eventually, but in today’s day and age, it is worth your time to take photos of the shipping box, along with a video of you unboxing your expensive, high-value items. I personally believe that without the video I made, it would be hard for me to prove my innocence.
Stay tuned.
Update: 3/1/2025 - Got my refund from Best Buy, but no explanation or any details about the investigation. Probably something they won’t share with consumers.
I mentioned earlier how Best Buy was going to give me a refund simply because I told them I didn’t receive a watch inside the package. It turns out I was misinformed by the person who helped me with this case. This actually makes a ton of sense though because if it was as simple as calling Best Buy and telling them there was nothing in the package, what is there to stop anyone from simply abusing that policy? They do want to do an investigation, which makes perfect sense.
They got back to me via email and kindly requested pictures of the product packaging and the shipping box. I one-upped that request with detailed photos and a video of me unboxing the watch strap box, tearing the seals and finding even more overly engineered cardboard.
I do expect to get a full refund eventually, but in today’s day and age, it is worth your time to take photos of the shipping box, along with a video of you unboxing your expensive, high-value items. I personally believe that without the video I made, it would be hard for me to prove my innocence.
Stay tuned.
Apple products: Why you should film your unboxing videos (part 1)
I bought an Apple Watch Ultra 2 from Best Buy Geek Squad Refurbished, and I had a “unique” unboxing experience. It was advertised as “Open Box Excellent” and when I opened the outer packaging, I got excited because the inner box that holds the Apple Watch still had the white plastic seals on it, signifying a brand new, unopened watch.
I tore the tabs off, and inside the box was the charger… and no watch.
I was not disappointed as much as I should have been, but I was actually impressed. How did they seal this package back up and make it look just like a brand new seal? I inspected the pull tabs on the seal and on the box, and nothing looked like it was put back together or jimmy-rigged in some way.
There was still the watch band to unbox, but this time I recorded it. The box felt suspiciously light, but the Alpine Loop is light too, so it was anybody’s guess if there was a band inside. When I pulled the sealed tab, there was an empty cardboard shell that holds the Alpine Loop.
Ouch.
The thieves have upped their game, but thankfully Best Buy is siding with the customer (me) and will be refunding me without even needing my video proving my innocence.
Not sure if other retailers/sellers will make it this easy to get a refund, but do yourself a favor and record your unboxings of any high-demand product, especially if it’s used.
Update: changed title to current title from previous title - PSA: Record your unboxings so you can prove your innocence.
I bought an Apple Watch Ultra 2 from Best Buy Geek Squad Refurbished, and I had a “unique” unboxing experience. It was advertised as “Open Box Excellent,” and when I opened the outer packaging, I got excited because the inner box that holds the Apple Watch still had the white plastic seals on it, signifying a brand new, unopened watch.
I tore the tabs off, and inside the box was the charger…and no watch.
I was not disappointed as much as I should have been, but I was actually impressed. How did they seal this package back up and make it look like a brand new seal? I inspected the pull tabs on the seal and on the box, and nothing looked like it was put back together or jimmy-rigged in some way.
There was still the watch band to unbox, but this time I recorded it. The box felt suspiciously light, but the Alpine Loop is light too, so it was anybody’s guess if there was a band inside. When I pulled the sealed tab, there was an empty cardboard shell that holds the Alpine Loop.
Ouch.
The thieves have upped their game, but thankfully Best Buy is siding with the customer (me) and will be refunding me without even needing my video proving my innocence.
Not sure if other retailers/sellers will make it this easy to get a refund, but do yourself a favor and record your unboxings of any high-demand product, especially if it’s used.
JD Vance gets told to take off his Apple Watch.
An open letter from Watches of Espionage, letting JD Vance know of the obvious security risks for a Vice President to be wearing a smartwatch.
Not a politically charged piece, just one that makes sense.
An open letter from Watches of Espionage, letting JD Vance know of the obvious security risks for a Vice President to be wearing a smartwatch.
Not a politically charged piece, just one that makes sense.
How to make your iPhone Passcode more secure without changing it.
Apple released Stolen Device Protection (SDP) in response to criminals successfully ruining people’s lives by using an iPhone’s password to reset the victim’s iCloud password.
In 2023 the New York Times did a report on this new tactic, summarized on TidBITS:
Watch the video, but in short, a ne’er-do-well gets someone in a bar to enter their iPhone passcode while they surreptitiously observe (or a partner does it for them). Then the thief steals the iPhone and dashes off. Within minutes, the thief has used the passcode to gain access to the iPhone and change the Apple ID password, which enables them to disable Find My, make purchases using Apple Pay, gain access to passwords stored in iCloud Keychain, and scan through Photos for pictures of documents that contain a Social Security number or other details that could be used for identity theft. After that, they may transfer money from bank accounts, apply for an Apple Card, and more, all while the user is completely locked out of their account.
And yes, they’ll wipe and resell the iPhone too. Almost no crimes like this have been reported by Android users, with a police officer speculating that it was because the resale value of Android phones is lower. In the video, Joanna Stern said a thief with the passcode to an Android phone could perform similar feats of identity and financial theft.
Apple’s response? Stolen Device Protection:
With Stolen Device Protection, some features and actions have additional security requirements when your iPhone is away from familiar locations such as home or work. These requirements help prevent someone who has stolen your device and knows your passcode from making critical changes to your account or device.
• Face ID or Touch ID biometric authentication: Some actions such as accessing stored passwords and credit cards require a single biometric authentication with Face ID or Touch ID — with no passcode alternative or fallback — so that only you can access these features.
• Security Delay: Some security actions such as changing your Apple Account password also require you to wait an hour and then perform a second Face ID or Touch ID authentication.
In the event that your iPhone is stolen, the security delay is designed to prevent a thief from performing critical operations so that you can mark your device as lost and make sure your Apple account is secure.
Thieves can still come after you if they see you entering your passcode because they’re hoping you don’t have this feature enabled, or they might not be aware of it themselves.
The goal shouldn’t be to prevent thieves from breaking into your accounts and your life, the goal is to prevent them from taking your iPhone in the first place. Even if you have all the safety measures in place and your phone gets swiped, you’re still without a phone, which will be expensive to replace and will take hours to get everything synced up again.
The best way to stop this is to hide your password when typing it in, but sometimes we might be in a hurry and forget to keep our guard up. Not to mention this type of attack is common in bars, so your guard is already lowered.
The next best thing? Change your password to an alphanumeric one.
You don’t have to actually change your password, but you do have to add something at the end of it. Like a period.
Say your passcode was “090708”. You can change your passcode and add a period, so your password is now “090708.” If the potential thief does see you entering your passcode, they will see the alphanumeric keyboard and will be more likely to skip past you because it’s almost impossible to really see what someone is typing. The keyboard is small enough, even on the Pro Max models, that your “fat finger” will obscure what you’re typing, compared to the huge numeric keypad.
It also helps to turn off haptics when typing in your code since people can’t hear how long your password is.
Over time, you’ll actually get faster at typing the alphanumeric code since it is all number based, but no one would know you would do such a thing…unless they read my blog.
I tried to be even slicker and just keep the exact same password even though I selected an alphanumeric option and keyboard, but the iPhone defaults back to a numeric keypad, so I had to add the period.
Apple released Stolen Device Protection (SDP) in response to criminals successfully ruining people’s lives by using an iPhone’s password to reset the victim’s iCloud password.
In 2023 the New York Times did a report on this new tactic, summarized on TidBITS:
Watch the video, but in short, a ne’er-do-well gets someone in a bar to enter their iPhone passcode while they surreptitiously observe (or a partner does it for them). Then the thief steals the iPhone and dashes off. Within minutes, the thief has used the passcode to gain access to the iPhone and change the Apple ID password, which enables them to disable Find My, make purchases using Apple Pay, gain access to passwords stored in iCloud Keychain, and scan through Photos for pictures of documents that contain a Social Security number or other details that could be used for identity theft. After that, they may transfer money from bank accounts, apply for an Apple Card, and more, all while the user is completely locked out of their account.
And yes, they’ll wipe and resell the iPhone too. Almost no crimes like this have been reported by Android users, with a police officer speculating that it was because the resale value of Android phones is lower. In the video, Joanna Stern said a thief with the passcode to an Android phone could perform similar feats of identity and financial theft.
Apple’s response? Stolen Device Protection:
With Stolen Device Protection, some features and actions have additional security requirements when your iPhone is away from familiar locations such as home or work. These requirements help prevent someone who has stolen your device and knows your passcode from making critical changes to your account or device.
• Face ID or Touch ID biometric authentication: Some actions such as accessing stored passwords and credit cards require a single biometric authentication with Face ID or Touch ID — with no passcode alternative or fallback — so that only you can access these features.
• Security Delay: Some security actions such as changing your Apple Account password also require you to wait an hour and then perform a second Face ID or Touch ID authentication.
In the event that your iPhone is stolen, the security delay is designed to prevent a thief from performing critical operations so that you can mark your device as lost and make sure your Apple account is secure.
Thieves can still come after you if they see you entering your passcode because they’re hoping you don’t have this feature enabled, or they might not be aware of it themselves.
The goal shouldn’t be to prevent thieves from breaking into your accounts and your life, the goal is to prevent them from taking your iPhone in the first place. Even if you have all the safety measures in place and your phone gets swiped, you’re still without a phone, which will be expensive to replace and will take hours to get everything synced up again.
The best way to stop this is to hide your password when typing it in, but sometimes we might be in a hurry and forget to keep our guard up. Not to mention this type of attack is common in bars, so your guard is already lowered.
The next best thing? Change your password to an alphanumeric one.
You don’t have to actually change your password, but you do have to add something at the end of it. Like a period.
Say your passcode was “090708”. You can change your passcode and add a period, so your password is now “090708.” If the potential thief does see you entering your passcode, they will see the alphanumeric keyboard and will be more likely to skip past you because it’s almost impossible to really see what someone is typing. The keyboard is small enough, even on the Pro Max models, that your “fat finger” will obscure what you’re typing, compared to the huge numeric keypad.
It also helps to turn off haptics when typing in your code since people can’t hear how long your password is.
Over time, you’ll actually get faster at typing the alphanumeric code since it is all number based, but no one would know you would do such a thing…unless they read my blog.
I tried to be even slicker and just keep the exact same password even though I selected an alphanumeric option and keyboard, but the iPhone defaults back to a numeric keypad, so I had to add the period.
ChatGPT can now read your Apple Notes on Mac.
Tim Hardwick from MacRumors:
OpenAI has expanded the capabilities of its ChatGPT app for macOS, adding support for Apple Notes and a range of popular third-party apps. The update builds on last month's release that introduced the ability to read on-screen content from select Mac apps…
OpenAI says that users maintain full control over which apps ChatGPT can access, and all data handling follows the same OpenAI privacy protocols as the app's regular conversation history. The expanded app integration feature remains exclusive to paid subscribers, including ChatGPT Plus, Pro, Team, Enterprise, and Edu users.
You do have to give ChatGPT permission to use the app, but that’s a lot of sensitive data to give to a 3rd party application, especially one as controversial as ChatGPT. People store all kinds of data in their Notes, including passwords, personal reflections, Driver’s license, medical and financial information, you name it.
I’m a free user of ChatGPT, so I have nothing to worry about, for now.
Tim Hardwick from MacRumors:
OpenAI has expanded the capabilities of its ChatGPT app for macOS, adding support for Apple Notes and a range of popular third-party apps. The update builds on last month's release that introduced the ability to read on-screen content from select Mac apps…
OpenAI says that users maintain full control over which apps ChatGPT can access, and all data handling follows the same OpenAI privacy protocols as the app's regular conversation history. The expanded app integration feature remains exclusive to paid subscribers, including ChatGPT Plus, Pro, Team, Enterprise, and Edu users.
You do have to give ChatGPT permission to use the app, but that’s a lot of sensitive data to give to a 3rd party application, especially one as controversial as ChatGPT. People store all kinds of data in their Notes, including passwords, personal reflections, Driver’s license, medical and financial information, you name it.
I’m a free user of ChatGPT, so I have nothing to worry about, for now.
Why you should use Water Lock on your Apple Watch
You can easily screw yourself over if you don’t use the Water Lock feature on the Apple Watch.
Whether you are swimming or taking a shower, you need to turn it on or else your screen will do crazy things.
Water conducts electrons like our fingers and can register touches and gestures on the touch screen. If you’re in the shower, the overwhelming amount of water can cause unpredictable behavior on your watch.
I have had the following two scenarios happen to me because I forgot to turn on Water Lock when jumping in the shower:
My mail app was open, and the watch had swiped left on an email to delete it. I noticed it just in time, but I could have unknowingly lost an important email I couldn't’ afford to lose.
In a separate incident, I was getting out of the shower and I heard voices coming to me. I glanced at my watch and realized that I was on an active call with my mom who was trying to talk to figure out what the heck was going on!
Do yourself a favor, and turn on Water Lock before jumping in the shower. That way you won’t have to worry about your watch accidentally opening apps, calling people, or deleting your emails.
You can easily screw yourself over if you don’t use the Water Lock feature on the Apple Watch.
Whether you are swimming or taking a shower, you need to turn it on or else your screen will do crazy things.
Water conducts electrons like our fingers and can register touches and gestures on the touch screen. If you’re in the shower, the overwhelming amount of water can cause unpredictable behavior on your watch.
I have had the following two scenarios happen to me because I forgot to turn on Water Lock when jumping in the shower:
My mail app was open, and the watch had swiped left on an email to delete it. I noticed it just in time, but I could have unknowingly lost an important email I couldn't’ afford to lose.
In a separate incident, I was getting out of the shower and I heard voices coming to me. I glanced at my watch and realized that I was on an active call with my mom who was trying to talk to figure out what the heck was going on!
Do yourself a favor, and turn on Water Lock before jumping in the shower. That way you won’t have to worry about your watch accidentally opening apps, calling people, or deleting your emails.
Passwords App on iPhone and Mac - one huge security difference.
I was reading about Microsoft’s AI based Recall feature, and I thought to myself, what if that feature was on the Mac? Would sensitive information be blurred out when screenshots were automatically being captured?
I was reading about Microsoft’s AI based Recall feature, and I thought to myself, what if that feature was on the Mac? Would sensitive information be blurred out when screenshots were automatically being captured?
The most sensitive app on your iPhone, iPad, or Mac is the Passwords app, and if it were to be “screenshotted,” it should blur the passwords.
On iOS and iPadOS, the Passwords app blurs all passwords when you take a screenshot. Even if you want to display the password in large type, the whole screenshot is a giant white blank screen, which is awesome. Even if the password field is obscured with dots (•••••••••••), taking a screenshot makes that whole field completely blank so you don’t even know how long the password is.
Here are 4 screenshots on iOS, showing the completely blank password field:
Now compare that to what you actually see when you are in the Passwords app on iOS (or iPadOS):
In general, iOS and iPadOS do a great job of obscuring your password when taking a screenshot in their app.
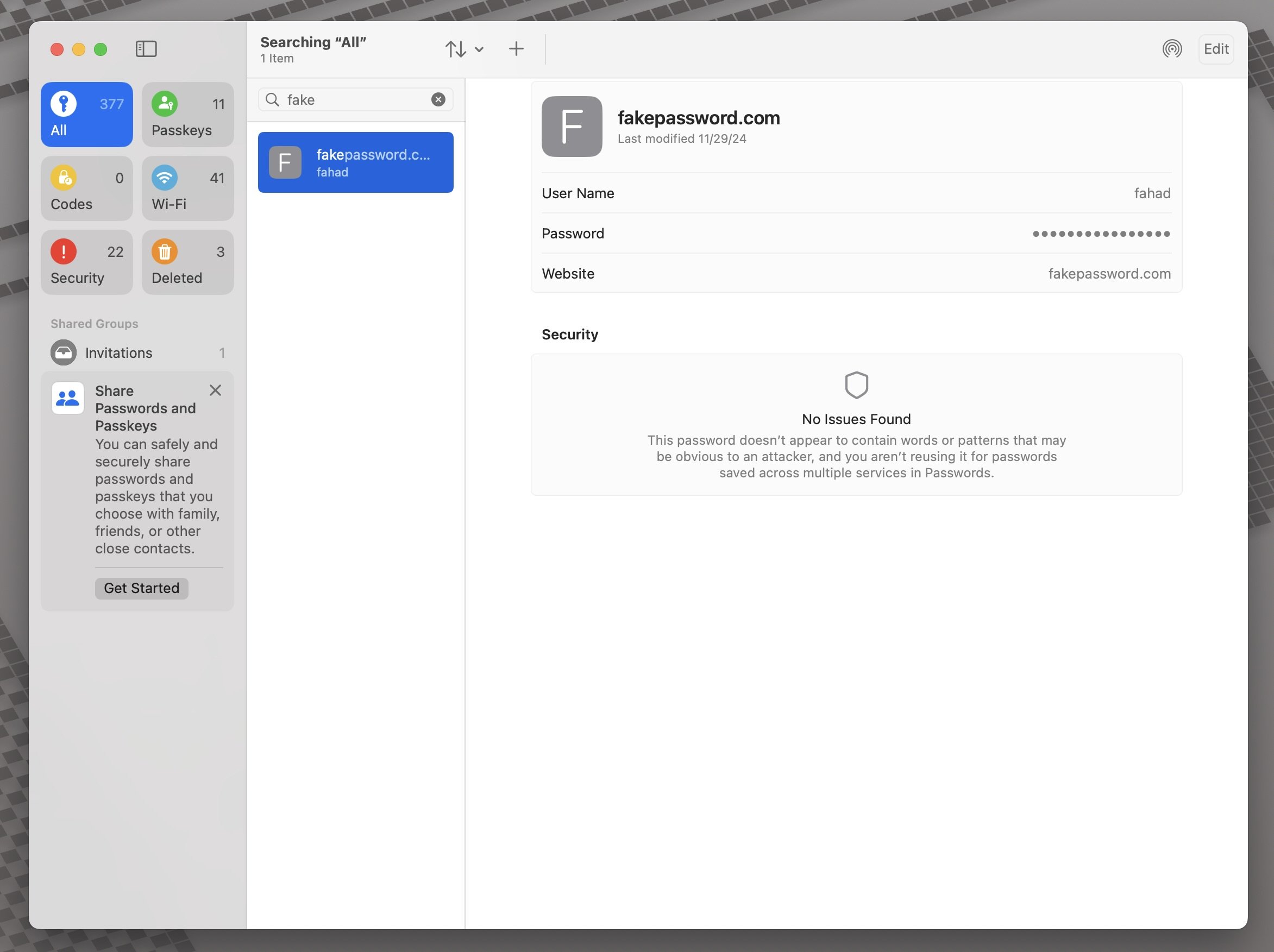
On macOS, that is not the case.
I opened the Passwords app and started taking screenshots, and it faithfully captures everything your eyes can see:
If your password is hidden with dots, you will see the dots.
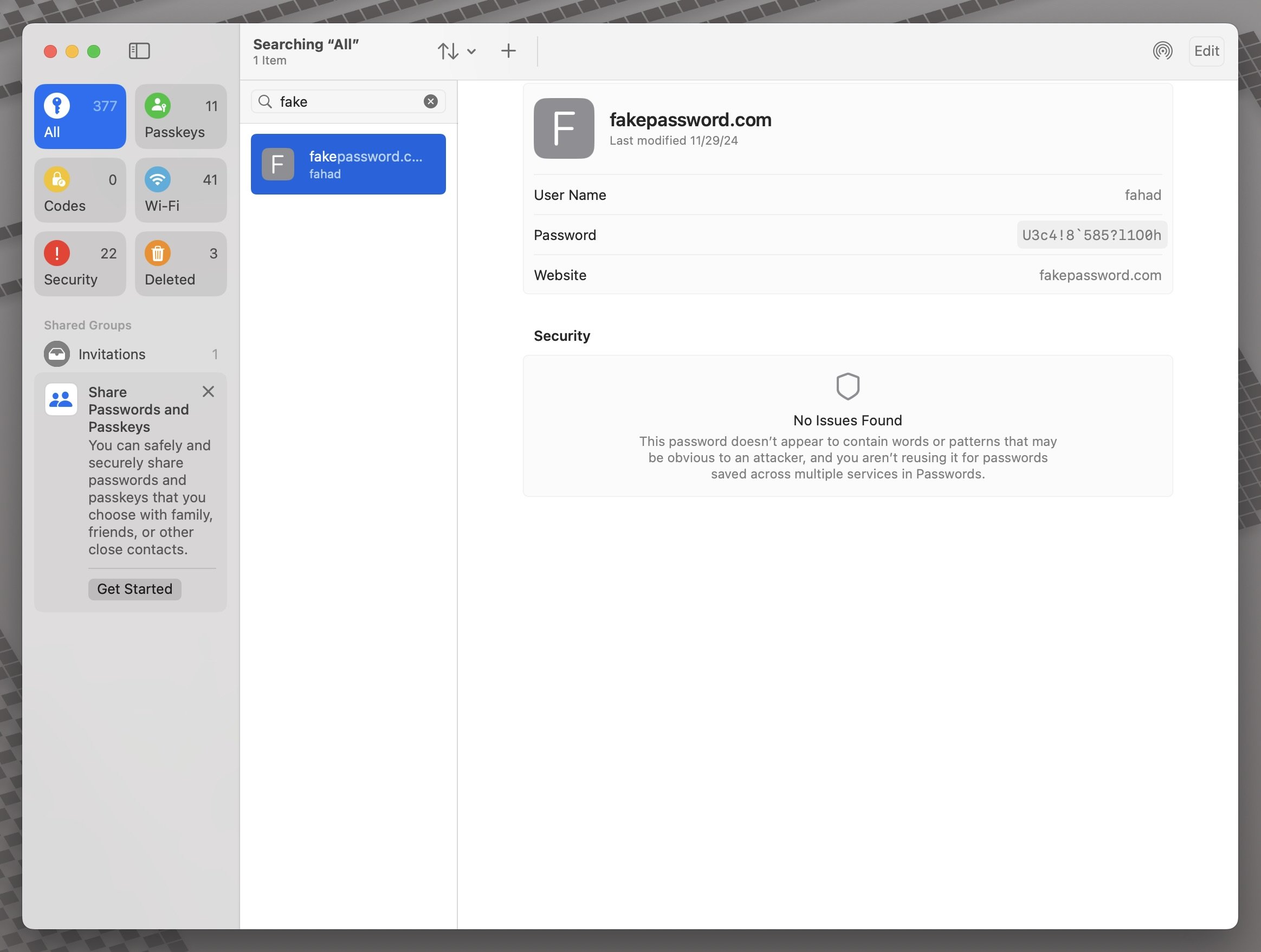
If you hover over your password revealing itself and then you take a screenshot, you will see the password.
If you choose the option to display the password in large type and then take a screenshot, you will see the password.
This is the complete opposite of iOS and iPadOS, and something Apple should address.
This might not be a security risk, but it can be in certain scenarios:
You save your screenshots to the cloud by default, making your passwords exposed to other individuals who might share the same iCloud folders as you.
You have multiple monitors and your passwords app is on your secondary (or tertiary) monitor. Many people don’t know or forget that when you take a screenshot, all of your monitors are being captured.
You have a custom mouse that has hotkeys for screenshotting, and you accidentally capture screenshots without your knowledge.
If this Recall feature was on macOS today, would you even want to open your Passwords app, knowing that the computer is taking screenshots in the background and capturing your sensitive information?
Imagine if your computer constantly was taking screenshots of your activity…
Not to worry, because Microsoft has a beta feature called Recall. Here is what it does in a nutshell:
If you opt in to the feature, then as you use your PC, a snapshot of your active screen will be saved every few seconds and when the content of your active window changes. Snapshots are also protected with Windows Hello, so that you are the only signed in user can access Recall content. Recall allows you to search for content, including both images and text, using the clues you remember. Trying to remember the name of the sustainable restaurant you saw last week? Just ask Recall and it retrieves both text and visual matches for your search, automatically sorted by how closely the results match your search. Recall can even jump back into the content you saw.
How safe is it?
To use Recall you need to opt in to saving snapshots, which are screenshots of your activity. Snapshots and the contextual information derived from them are saved and encrypted to your local hard drive. Recall does not share snapshots or associated data with Microsoft or third parties, nor is it shared between different Windows users on the same device. Windows will ask for your permission before saving snapshots. You are always in control, and you can delete snapshots, pause or turn them off at any time. Any future options for the user to share data will require fully informed explicit action by the user.
Do we really need our computer to constantly take screenshots of our online activity? Sounds overboard, even if the information is encrypted locally. I know that if Apple were to do something like this for the Mac, I would keep it disabled. Thankfully this feature is an opt-in feature for Windows users.
Since it is still in beta, there are still lots of security risks since Recall has trouble discerning sensitive websites and screenshots sensitive information.
Not to worry, because Microsoft has a beta feature called Recall. Here is what it does in a nutshell:
If you opt in to the feature, then as you use your PC, a snapshot of your active screen will be saved every few seconds and when the content of your active window changes. Snapshots are also protected with Windows Hello, so that you are the only signed in user can access Recall content. Recall allows you to search for content, including both images and text, using the clues you remember. Trying to remember the name of the sustainable restaurant you saw last week? Just ask Recall and it retrieves both text and visual matches for your search, automatically sorted by how closely the results match your search. Recall can even jump back into the content you saw.
How safe is it?
To use Recall you need to opt in to saving snapshots, which are screenshots of your activity. Snapshots and the contextual information derived from them are saved and encrypted to your local hard drive. Recall does not share snapshots or associated data with Microsoft or third parties, nor is it shared between different Windows users on the same device. Windows will ask for your permission before saving snapshots. You are always in control, and you can delete snapshots, pause or turn them off at any time. Any future options for the user to share data will require fully informed explicit action by the user.
Do we really need our computer to constantly take screenshots of our online activity? Sounds overboard, even if the information is encrypted locally. I know that if Apple were to do something like this for the Mac, I would keep it disabled. Thankfully this feature is an opt-in feature for Windows users.
Since it is still in beta, there are still lots of security risks since Recall has trouble discerning sensitive websites and screenshots sensitive information.